With expertise in securing applications.
Walnut Security Services consists of dedicated, professional experts with the constant aim to offer unique services and support to our clients.
Our reason to exist is to support customers in improving the security posture of their applications or infrastructure, ensuring continuity and sustainably maximum value.

With expertise in securing applications.
Walnut Security Services consists of dedicated, professional experts with the constant aim to offer unique services and support to our clients.
Our reason to exist is to support customers in improving the security posture of their applications or infrastructure, ensuring continuity and sustainably maximum value.

Securing our Valuable Clients
Walnut Security Services mission is to provide highly professional cybersecurity services, thanks to our team for its continuous commitment in learning new attacks and reproducing it in a secure environment.
Our motto, passion at work, makes all the difference. It separates the extraordinary from the ordinary and pushes towards a relentless quest for perfection. Working with passion is one of the key aspects of our success.
WHY CHOOSE US
Our high-level quality services in cybersecurity are the top priority and to be never compromised to deliver top-notch security services

Our company has the best cybersecurity experts who are the pillars for providing quality aided penetration testing services

Our company, WSS is built on some core principles and integrity to never compromise with our clients vital information

We ensure to manage and secure all the essential information and data of our clients in highly encrypted storage

We aim at providing supervision and taking care of your business model from the standpoint of cybersecurity

We have adopted a unique pricing model for all our clients. Rest assured to get the best price in the industry

Our highly industrious team is the main reason we can promise quality services to our clients with confidence and pride

Our highly professional experts are constantly upgrading themselves with the latest attacks to ensure robust security

We know that your organization’s security is of utmost importance. Thus we are available at your service 24*7
Excellence in providing
cybersecurity service to excel business
We consult, advise, support, and make your application or infrastructure more secure than ever before by providing below professional services
To discover security problems and ensure that all vulnerabilities are covered during the security assessment process, we use the most recent OWASP Top 10 and our own approach

We employ android application penetrating services, which covers real-time testing of android applications from a security standpoint, to uncover security issues in an application

Penetration Testing
Our highly efficient iOS penetration testing makes your iOS application safe against attackers. After thorough analysis, we come up with the best strategy to secure applications

Code Review
To secure code, our specialized task force performs a manual and/or automated review of an application’s source code in order to identify security-related flaws in the code

Centre (SOC)
Our SOC management experts protect your system from cyber threats by continuously monitoring. Our SOC management actively identifies, investigates, and counters any cyber attack

We discover, configure, and provide actionable recommendations to improve your Google Cloud Platform (GCP) security posture using our penetration testing service

Penetration Testing
API is proven to be the most popular surface for gaining access to servers. We protect your web and mobile applications and strengthen any API weakness with our API penetration tests

Engagements
Our team of experts checks the security of your organization against real-time attackers with a group of advanced tests and reveals the weakness and the options for an attacker

Penetration Testing
We identify vulnerabilities and reveal the real-world threats they may pose for your business. Our well-rounded pentesters safeguards your network from unauthorized access

Penetration Testing
A thorough vulnerability evaluation and penetration testing of AWS infrastructure solutions can assist them in addressing this issue and ensuring a solid security framework

Penetration Testing
We perform an intensive Azure penetration test to uncover the misconfiguration and vulnerabilities to eliminate the security risks from your Azure cloud

Compliance
We deliver HIPAA Compliance to ensure your customers are promised privacy. Our compliance report saves businesses from sensitive PHI loss and violation fines

Compliance
We ensure that your system processes and secures your customer information efficiently. With SOC-1 compliance report, we make your customers believe in your organization’s security posture

Compliance
We affirm the operational efficiency and high-level security of systems with our detailed 5-trust criteria-based SOC-2 report. So your customers are assured of the efficiency of your system

Compliance
We declare your business to be at the apex of information security with our ISO 27001 compliance audit. Secure your operational system, communication system, services, and workstations with WSS

Compliance
With PCI DSS Compliance, we make card transactions for your business safer. We safeguard your payment system from theft and violation of the sensitive data of the cardholder

Secure Review
We deliver continuous container security to protect the applications and performance of the container. Our security tools defend your infrastructure against cyber threats

Development
We develop applications to provide robust performance with smooth operations, secure framework, and effortless UI to bring the maximum value to your business
Training
We provide attack and defence training here we teach you how attackers discover and exploit vulnerabilities in the real world

Security
It is a new research area that addresses security issues that arise during the execution of smart contracts in a blockchain system

Hunting
We provide threat hunting, a process that combines security tools and threat intelligence with human instinct
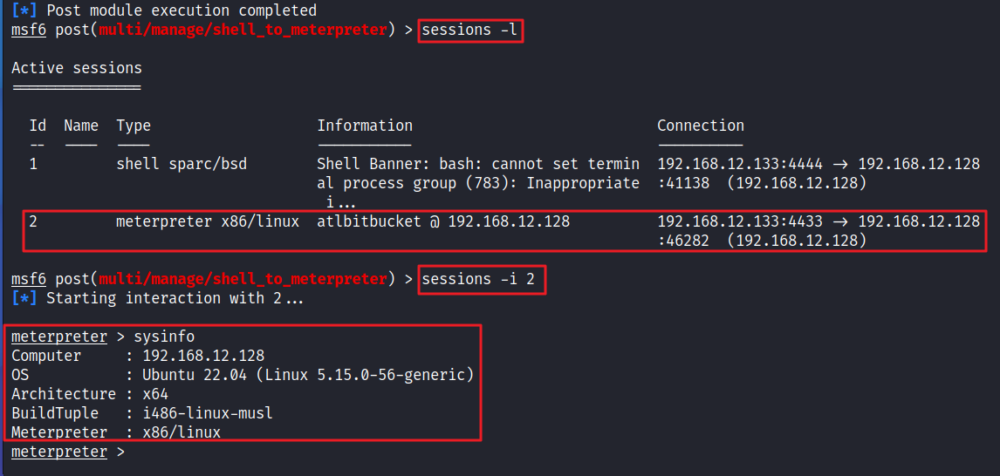
How Does Walnut Security Works?
We believe in interacting with our clients to collect all essential details regarding the requirements. Prior to that, we then discuss pricing, methodology, demo report, and deliverables
It is vital to plan attack surfaces based on the information collected. With all the valuable information available, we then plan how to apply and strategize our work depending on the requirements
We simulate real world attacks to identify the vulnerabilities and weak spots in application or infrastructure. We collect proof that can be taken as evidence to generate a final report
After completing the assessment taking all the required actions and steps, we gather all the necessary information for preparing the final report. Draft report will also be shared prior to final report
As discussed in the initial stage, we share the final report, PPT file and excel sheet. This helps in tracking the timeline to patch identified vulnerabilities and providing a final report’s overview
We are determined to be able to help them to understand the criticality of identified vulnerabilities and its impact. We ensure to track every little inquiry to answer as fast and accurately as possible
We cover a broad spectrum of planning
& security projects
Our professional services give you an insight into your organization’s security posture and accept a wide range of projects that have both challenged and excited us in equal measure. We are not bound by any limitation and seek pragmatic solutions that provide high-quality pentesting services
What our customers are saying about us
See what WSS clients have to say about a variety of services that we provided for their organization

Nicole
DirectorWe are glad to choose WSS for the web application penetration testing. We got a vulnerability report explaining each point in-depth on how to secure our application.

Connar
CISOI would like to recommend WSS for its penetration testing service. They have a highly qualified team providing professional services.

Alberto
CEOThanks, WSS for providing insight into our missing compliant pieces. Your service really helped us achieve our target to became a PCI-DSS compliance company.

Carlos
CTOWSS did an excellent job for our organization by securing hundreds of our valuable assets. We really liked their service and the support they gave us.

Gerald
CEOWSS did impressive work by completing our long project in a short duration. They always kept us satisfied with their way of working.
150
Completed Projects
20
Professional Team
100+
Satisfied Clients
5+
Worldwide Partnership
Ready to schedule your service?
When you hire us for cybersecurity services, you know you’re getting highly qualified professionals who have the expertise and experience to make sure your project is secure and hackproof